| Title | Validate Zscaler Security Service Edge (SSE) security effectiveness with AttackIQ Breach Attack Simulation Tool |
| Objective | Proactively find and reduce security gaps |
| Requirements |
|
| Scope |
|
| MITRE Techniques ID |
|
Executive Summary
One of the biggest pain-points that big organisation face is trying to find out the effectiveness of their security controls in place. Back in the days when the breach attack simulation tool did not exist, the only way to validate the security tools in place was by placing an offensive red team and threat hunting exercises.
Both ways are conventional jobs to be carried out. In fact, in order for the security teams to come out with the test, it takes quite some time to get it ready. One of the reasons is that, prior to performing the activity, it requires mutual approval from multiple stakeholders. In most cases, the activity they usually do is harmful to the production environment.
Now, we’ve got the chance to test and research the new tool on the market. It is called the AttackIQ Breach Attack & Simulation tool. To put it simply, this AttackIQ Breach Attack & Simulation is an advanced computer security testing method whereby any simulations performed are able to identify vulnerabilities in security environments by mimicking the likely attack paths and techniques used by malicious actors. The good thing is, it is also able to help organisations validate their critical security controls’ effectiveness and efficiency with the objective of ensuring their security controls are able to prevent and detect any cyber threats with just a few clicks.
Breach Attack Simulation Activity
For this activity, first we deployed a Zscaler client connector on user’s machine running Windows 10, an agent based Zscaler SSE (Security Service Edge) and AttackIQ agent.
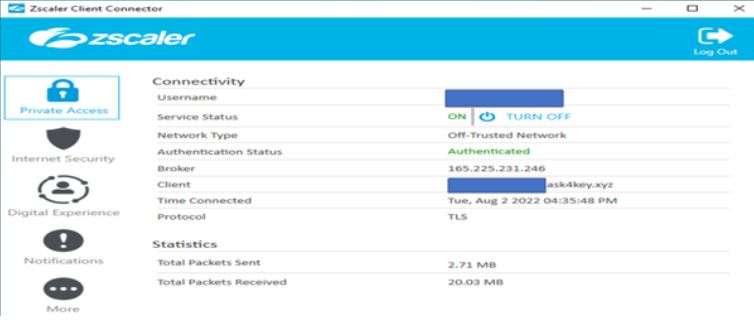
We will be using a typical content filtering scenario mostly for proxy-based, next-gen firewall and anti-virus security tools. Additionally, we included the most common ransomware that is still active in the wild, BlackCat ransomware.
For more info about this threat, check out this link:
The typical questions that come from the board when there is news about new threats will be asking you “are we secured enough from this new threat?” Now, let’s assume that you got this question from the board where the new ransomware in the wild called BlackCat has started targeting the same industry/sector as you.
From the AttackIQ platform, this BlackCat ransomware is already there as pre-built in and we will be using it together with another test scenarios.
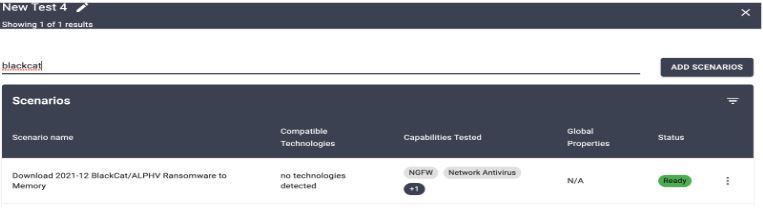
And we picked one agent for this simulation test.
There are more than 1 scenarios included other than one mentioned above (BlackCat Ransomware). For this we also added another scenario in total of 459.
Under test 4 (custom), all scenarios are under several categories such as content filtering, NGFW and network antivirus.
Then, we ran the first simulation test and wait until it is complete.
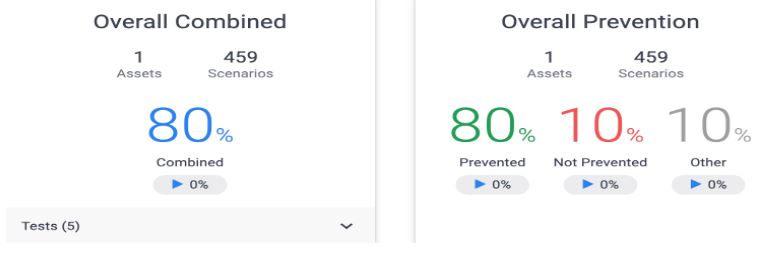
After the first simulation test is complete, we were able to see the results of the security gaps in our Zscaler SSE policy whereby overall prevented is 80% and 10% not prevented.
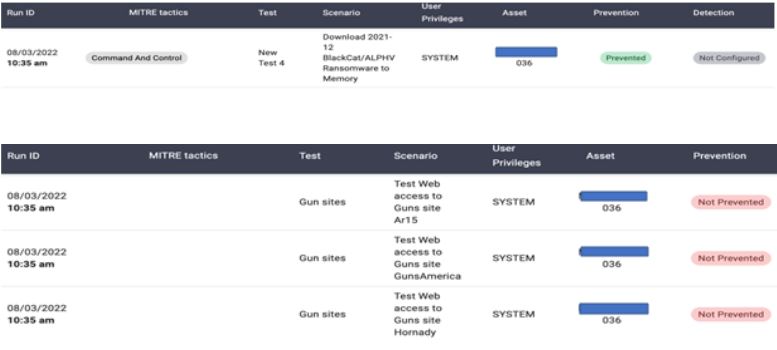
Now, we will need to know what are those 10% not prevented all about. We will drill that down and see what we can do to reduce these security gaps.
We found out that the BlackCat is prevented which is good and the other one where the Gun Sites was not prevented.
Now, we know that we have to ensure our Zscaler SSE is able to prevent this Gun sites as part of remediation process. Shall this access prevention be included in our Information Security Policy of Web Application Access in our organizations, we then should block these Gun Sites for the user in Zscaler Admin Portal.
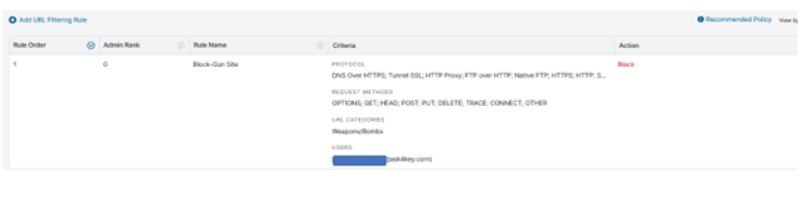
Now, we ran again the second test under the same assessment. From here, we found out the results as shown below.
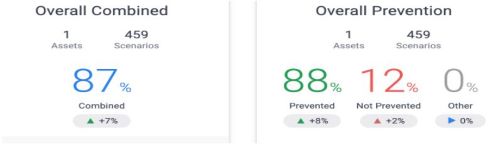
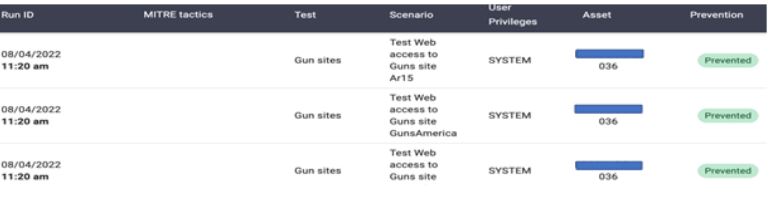
Now, as what is shown below, it seems it was able to prevent all of them after we re-ran the second simulation test.
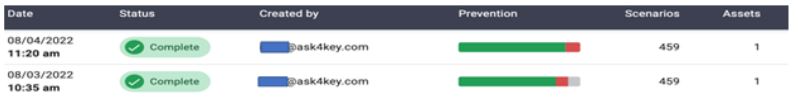
Conclusion
The good thing running this simulation test is that, like AttackIQ Breach Attack & Simulation tool, it was able to give us an accurate information about the security tools that we have by showing us the security gaps for each tool we test. We can see the prevention ratio comparison of the test before (08/03/2022) and after (08/04/2022), right after we setup the Zscaler SSE policy to block or prevent certain scenarios as shown below.
As we know, we now live in an era of many sophisticated threats in the cyber world. The never-ending threats that are often financially-motivated. Most organisations are seeking a solution to ensure their critical security controls in place are always top-notch and always ready to prevent and detect any new or even old threats. Yet, the board members usually need solid proof of knowing and seeing the results for each one of them, and therefore, a breach attack and simulation test tool like AttackIQ could help any organizations to reduce security gaps and embracing security maturity as part of their security programme.