| Title | Common Threat Actors TTPs: Execute Ransomware and Delete Volume Shadow Copies |
| Objective | Auto-Containment for Immediate Blocking |
| Requirements |
|
| Scope |
|
| MITRE Techniques ID |
|
Executive Summary
Most ransomware threats normally will perform to delete volume shadow copies in order to prevent the recovery of a corrupted or encrypted system. This is to ensure that the victim would not be able to perform recovery from the built-in operating system data.
Therefore, for this time around, we came out with a real simulation attack whereby the compromised machine is already backdoored with our C2 and the attacker were able to perform to encrypt the machine’s data with ransomware and will try to delete the volume shadow copies.
The scenario assumptions:
- The Windows 10 is already compromised with external C2 for many months and attacker keep on monitoring and waiting for the right time to execute ransomware.
- Attacker were able to deploy a C2 through a watering hole attack and put the C2 malware into sleep for a month and reactivate it on a specific date.
- Microsoft Defender was turned on and the attacker was able to perform AMSI bypass.
The objective of this simulation is still the same as what is written in our previous blog, aim to contain compromised machine from communicating with another servers or end users internally. It is therefore, Zscaler Active Defense must be integrated with any security tools in place. In our case, we will be integrating Zscaler Active Defense with Fortinet Fortigate Firewall. Go to our previous blog, here for more info.
Real Attacks Simulation
Since the machine is already been compromised for months, the attacker was waiting for the right time to execute his ransomware on the victim’s machine. It is therefore, the attacker performed the following to drop his ransomware.exe.
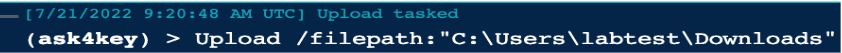
Then, the ransomware.exe executed and encrypted all the files in the compromised machine.
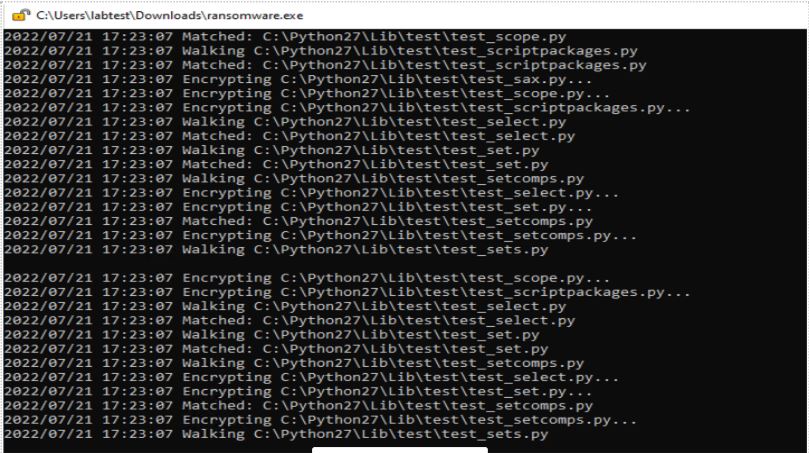
Encrypting all files as it supposed to.
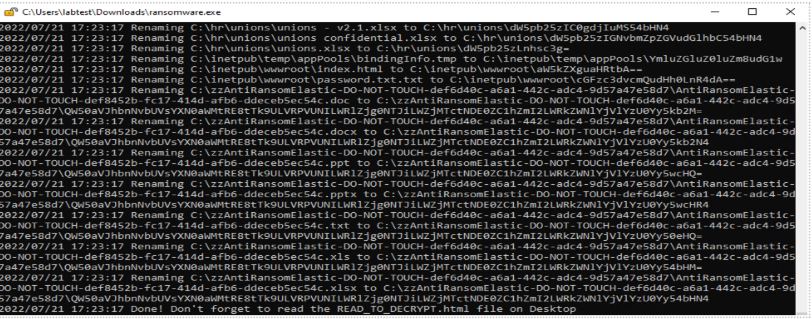
Finally, ransomware.exe were able to encrypt all files and by right, the machine would not be accessible again because the Zscaler Active Defense should be able to detect it and send the threat details to Fortinet Fortigate Firewall for a containment. We shall check from Zscaler Active Defense and Fortinet Fortigate Firewall.
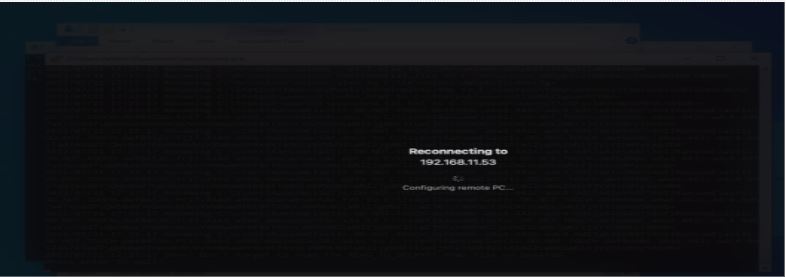
The compromised machine is no longer accessible.

And from the Zscaler Active Defense, it was able to detect the malicious activity and from here, it will be sending the threat details to Fortinet Fortigate Firewall for containment purposes.
![]()
Normally, the threat actor will perform to delete volume shadow copies right after encrypting the files with the ransomware. We tried to execute this and failed as it seems.
![]()
And from Zscaler Active Defense, it was able to catch the activity.
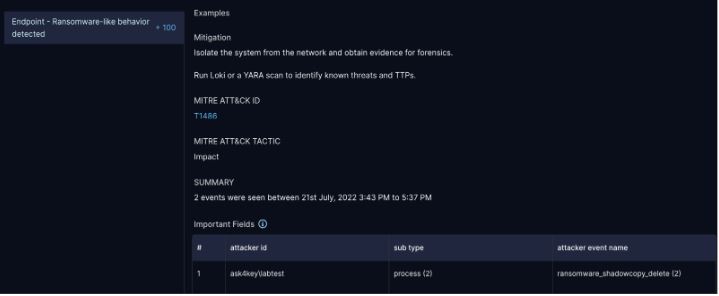
Conclusion
From the activity we made so far, it is obviously that the Zscaler Active Defense were able to catch and trigger common adversary tactics and techniques and contained them within less than 1 minute. This is a good sign because as a Security Analyst or Security Specialist, a MTTR (Mean Time to Respond) and MTTD (Mean Time to Detect) are vital to ensure the efficiency and effectiveness of any security operations are on the highest gains which literally helping them by displaying Security Operation progress in order to prove the value of the security program to the board members.